It’s often been said that the jails and prisons in the U.S. operate on a revolving door system, with many of the same prisoners returning to incarceration time after time after time. Sadly, that’s a mostly true statement.
With nearly 2.5 million people crammed into U.S. prison and jail facilities, or on probation or parole—3,789,800 on probation and 870,500 on parole (2015 stats), well, that equals to approximately 1 out of every 37 people in the U.S. is currently under some sort of supervised correctional status.
Yes, America can proudly boast (note the sarcasm) that we hold 25% of the world’s prison population. That’s a pretty staggering number considering the U.S. accounts for only 5% of the world’s population. Those numbers don’t mean much, you say? Well, let’s approach from another angle … our wallets. Each year the U.S. spends between 74 and 80 billion dollars on incarceration. That’s BILLION dollars.
Sure, most citizens don’t want to be bothered with felons and other law-breakers. You know, out of sight/out of mind. But it’s not quite that simple. You see, Isaac Newton had the right idea when he mused, “What goes up must come down,” because the same applies to prisons, jails, and inmates—what goes in must come out. That’s right, the majority of people sentenced to jail or prison must be released at some point, and those former prisoners are generally released back into their former communities.
What happens to former prisoners when they do finally make it back to their old neighborhoods? That’s a question most people don’t consider because the ex-con’s troubles don’t pertain to “most people.” Unfortunately, though, an inmate’s troubles affects everyone. Remember the 80 billion dollars it costs to incarcerate and supervise those millions of prisoners? Well, U.S. taxpayers are responsible for paying that whopping bill.
Doesn’t it makes sense that we should try to address the problem instead of throwing good money on top of bad? Obviously, incarceration isn’t always the correct answer to every case, because many offenders just keep coming back after they’ve “paid” their debt to society.
Let’s address recidivism …
… and why I think it occurs so often. First of all, I have many years of experience working in both corrections and in law enforcement, which means I’ve seen the system in action, from all sides. I’ve also owned a business where I employed a few former inmates, men who’d received prison sentences resulting from my investigations. Ironic, huh? Yes, I honestly believe in second chances.
What do former prisoners face upon their release? (these may vary depending on location)
1. They must, on a regular basis, check in with a probation or parole officer.
2. They must have an established residence.
3. Many drug and sex offenders must register with the local police, advising officials where they’ll be residing and working.
4. They must maintain employment (in some areas this is a discretionary requirement imposed by the court).
5. They’re required to complete a monthly report detailing their earnings, address changes, if any, employers name (probation officer will visit the job site and home), drug offenders must submit to urine testing, all must submit vehicle information, record of purchases (many probationers may not possess credit or debit cards), and they’re encouraged to further their education (This is a bit of a catch-22 for some since drug offenders may not receive grants to attend college. Murderers, yes, but drug offenders, no).
Some companies refuse to hire people who’ve been convicted of felonies … any felonies.
A vast number of employers absolutely will not hire felons and, as I stated above, drug offenders are not eligible for student loans. In fact, many felons are legally banned from working in certain professions, such as:
- airport security screener
- armored car crew member
- bank teller
- child care provider
- delivery driver
- health care positions with direct patient contact
- public safety officer
- residential installers
- apartment or condo maintenance
- jobs that require handling money
- Realtor
- Some volunteer programs refuse to accept felons (any felon)—nature programs, animal shelters, libraries, etc.

Even when a felon finds a job he is subject to a list of restrictions, including (this is only a partial list, and it may vary from area to area):
- Agents /officers must be allowed to visit worksite and/or speak with a supervisor to discuss client’s performance, progress, and accountability
- Cannot work in a position that serves alcohol
- Cannot work with minors
- Cannot work with vulnerable adults
- Employment must be within or close to a supervision district so that agents may visit the worksite
- Not allowed to use or have contact with devices that host a computer modem (i.e. any device that can access the Internet)
- Cannot travel outside area or state (affects delivery drivers)
A few professions do hire convicted felons, but the list is short. And, this is still entirely up to the company. Some do not employ those who’ve been convicted of crimes.
Professions often available to convicted felons:
- Warehouse work
- Maintenance and janitorial positions
- Food service (no alcohol)
- Production and manufacturing
- Assembly
- Construction
- Landscaping

In addition, many convicted felons are banned from living in publicly assisted housing (section 8), or worse.

So, you see, without a job, or with the limited occupations to choose from, and without housing and educational opportunities, it’s darn tough for a former prisoner to make it on the outside.
To top it all off, the convicted felons never actually “pay their debts to society.” The stigma of being a “convicted felon” hangs over their heads for life. This is especially true for those who were convicted of federal offenses. Some states allow convicted felons to vote in elections (others do not).
Still, felons, even one-time first offenders convicted of minor, non-violent felonies lose their right to own firearms and other weapons, their right to vote, student loans, housing, etc. And these restrictions are for life.
Second Chances!!
Wouldn’t it make sense to give the non-violent offenders a second chance, by removing the “convicted felon” status after, say, 10 years of living a productive, crime-free life. At least then they’d have the opportunity to return to school, live in better neighborhoods (away from criminal activity), find a decent job that would help support their families and take better care of their children, who, by the way, also suffer by being forced to live in poor conditions.
Having a second chance and goals to work toward could be part of the solution to the “prison problem” in this country. Now, I’m not talking about hardcore career criminals and repeat offenders. Nor am I including violent offenders. Most of those thugs need to remain behind bars for as long as we can keep them there. And I certainly don’t believe that every inmate would take advantage of the opportunity if presented to them. But there would be many who would work hard to achieve the goal and finally be able to put the mistake behind them for good.
If this helped keep just a small portion of the recidivists out of prison, the results could be huge. Families could remain together, children would grow up with two parents in the home, employers might find top-notch employees, the former inmates could become better educated and productive members of society, and taxpayers would save approximately $30,000 per year per inmate. Not to mention that instead of costing taxpayers, the non-recidivist would become a taxPAYER.
New York City is set to begin a program that offers guaranteed employment to each of their 8,500 inmates as they leave jail. These jobs are to be short-term, low skill level employment—cooks, restaurant bussers, or construction flaggers, etc.
The $10 million program will apply to inmates no matter what crime they’ve committed, even if they’re on the sex offender registry. Everyone gets a job. Everyone, including murderers, rapists, robbers, and …
I’m not sure the New York City plan is the best idea in the world, but they’re making an effort to address the issue. While not the most well-thought-out plan, it could still give former prisoners a much-needed boost of confidence, self-worth, and desire to do better. It could also go a long ways toward reducing the intense shame many feel after their release.
Anyway, that’s my two cents on the matter. What do you think? A second chance for some, or lock ’em up and forget about them? Remember, though, most of those who go in must come out at some point.

Of course, there is the issue of private prisons that have contracts with the government … contracts that promise a minimum number of inmates will be sent their way. We must also remember that the private prisons are a big, money-making industry with stockholders.
And then there’s the food industry that makes a bundle off the prisons. And the construction companies, the jobs for officers, stock brokers medical staff, administration, the vehicle contracts, the weapons contracts, dog food (canines), condiment sales (I once sat next to a woman on a plane who was on her way to a huge nationwide prison food convention. She was in charge of condiment sales to prisons and jails—packets of mustard, ketchup, and mayonnaise, along with napkins, and sporks—a multi-million-dollar industry)
Inmate phone calls are EXPENSIVE!
Let’s not forget the prison phone systems, where a collect call can go for fees as high as nearly $300 for just one hour of conversation. Think about it for a second. A call for a kid’s birthday, a mother’s sick, etc. $300 for an hour of family time is a tough expense for most families.

A portion of that whopping phone bill goes back to the prison in exchange for a contract with the provider. Again, it is the family who shoulders this burden since inmates don’t earn anywhere near enough money to cover the expense, yet, officials encourage strong and regular family contact.
Anyway, you get the idea.

A very happy prisoner. I asked why the big smile. Her reply was, “Things could be worse. At least I’m alive and healthy.” Notice the blue phone and its cord at the right side of the photo. Collect calls only.
Private Prison Profits Big Time!
CoreCivic stock at the time of the original posting of this article (now revised), stood at $34.70 per share. Today (May 21, 2018), shares were at $20.65. Still, the “people business” is certainly booming when others are failing miserably.
To read more about CoreCivic, visit their website by clicking here.
- CoreCivic, one of the largest private prison companies in the world, is the company formerly known as Corrections Corporations of America.
- CCA houses approximately 90,000 prisoners in over 65 facilities.
- CCA has been the center of controversy over the years. Most of their troubles, but definitely not all, were related to cost-saving practices that included inadequate staff, extensive lobbying, and lack of proper cooperation with legal entities. CCA swapped amid the ongoing scrutiny of the private prison industry. Many believe the name change of private prisons is due to their rising unpopularity among the public, and to avoid a connection to past bad and illegal behavior.
Another for-profit “private prison company,” Wackenhut Corrections Corporation (WCC), now a subsidiary of G4S Secure Solutions changed its name to the GEO Group, Inc. It, too, houses thousands of prisoners around the world.
The Geo Group alone reported GEO reported total revenues for the fourth quarter 2017 of $569.0 million. This figure up a bit up from $566.6 million for the fourth quarter 2016. 2017 revenues include $2.8 million in construction costs associated with the development of the Ravenhall Correctional Centre in Australia.
Yes, private prisons are a big business.
#prisonreform
#secondchances
Life on the inside


Above and below – inside a small county jail where conditions were truly deplorable.

Showers drained into the corridors.

Jailer entering corridor.
Jail Pods

Above – Inside a shipping container “pod” that was converted into a dormitory-style jail cell. This pod is located inside a parking garage outside an overcrowded county jail.
Below – Space between two modules serves as the recreation yard. Absolutely no sunlight to be found, anywhere. Nothing but concrete, sewer pipes, exhaust fumes, and prisoners.

Below – In this county jail, prisoners are brought to these small rooms where they “visit” with family members seated on the opposite side of the window. The family’s room is a mirror image of the inmate’s visiting room. The view below is from the inmate’s side of the glass.

Overcrowding is a big issue within some prisons and jails. As an answer to their growing space problem, this county jail (below) installed steel beds in the hallways, outside the already packed jail cells.




Looking out from inside the trustee cells.
Hallways and corridors were narrow, making for dangerous conditions for the jailers. The jail was heated by steam (boilers) and radiators were there, but scarce. There was no heat inside the cells. And, there was no air conditioning whatsoever. The only airflow came from small widows. Here, you can see one of those windows (top left corner), open and tilted in toward the cells. The electrical cord is connected to a portable TV sitting on the wonky shelf, also at top left next to the window.

Narrow corridors are dangerous!
Makeshift antenna controls were fashioned from string or wires. Not allowed, but prisoners will be prisoners …

Wires to rotate rabbit-ear antennas from side to side to help receive a better picture. No cable!
Below is an image of an isolation cell (“the hole”) where unruly, violent prisoners in this jail are housed. No bed, no sink, no toilet. Merely a drain in the floor to use for, well, you know.








 Trooper Samuel Newton Bullard, 24
Trooper Samuel Newton Bullard, 24 Police Officer Amy Caprio, 29
Police Officer Amy Caprio, 29 Officer Thomas Coulter, 25
Officer Thomas Coulter, 25 Officer Ayrian Williams,
Officer Ayrian Williams,



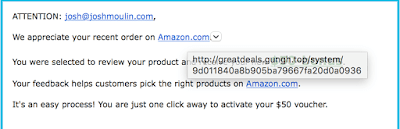
 If you have been following this blog series, you know that the
If you have been following this blog series, you know that the 
 Josh Moulin serves as a trusted advisor to federal government IT and cybersecurity executives. Previously, Moulin was the Chief Information Officer for the Nevada National Security Site, part of the U.S. Department of Energy’s Nuclear Weapons Complex and before that spent 11 years in law enforcement including 7 years as the commander of a cybercrimes task force.
Josh Moulin serves as a trusted advisor to federal government IT and cybersecurity executives. Previously, Moulin was the Chief Information Officer for the Nevada National Security Site, part of the U.S. Department of Energy’s Nuclear Weapons Complex and before that spent 11 years in law enforcement including 7 years as the commander of a cybercrimes task force.






















 Officer Lance C. Whitaker
Officer Lance C. Whitaker Officer E. Paul Morris
Officer E. Paul Morris







 All this without the messy powders that never seem to wash away. The KS Imager can also be used to greatly enhance prints developed using cyanoacrylate fuming (Super Glue).
All this without the messy powders that never seem to wash away. The KS Imager can also be used to greatly enhance prints developed using cyanoacrylate fuming (Super Glue).