Josh Moulin: What Information Is In Your Digital Images?
Josh Moulin
Digital pictures and video have transformed our lives. I have so many pictures and videos of my kids that by the time they are in college, I’ll have Terabytes of data. It is so easy these days to capture anything with a digital image. There is no need to worry about having film developed, or being careful to only take good pictures since you only have a limited amount of pictures left on the roll in your camera. Now, we’re only limited by the amount of storage space our digital devices have. As an example, the MicroSD card in most of our smartphones can contain over 18,000 pictures.
MicroSD cards now have a capacity of up to 64 GB
Often, digital images are involved in criminal investigations. Imagine the treasure-trove of information that can be obtained from a cell phone, tablet, or digital camera when it is seized from a suspect. In my experience, those involved in criminal activity just can’t help themselves when it comes to documenting their criminal activity in pictures or video. In literally hundreds of cases, I found suspects taking pictures of themselves using drugs, vandalizing property, committing arson, abusing children, and in some cases, even murder.
While having picture or video evidence of a suspect actually committing a crime is the type of evidence that makes a prosecutor excited about a case, the digital image is just the beginning of the story. Imagine if we could tell what camera was used to take a certain picture that was found on the Internet, or could link an image found on a suspect’s computer with their personal phone or digital camera found at their home? This is all possible thanks to something called metadata.
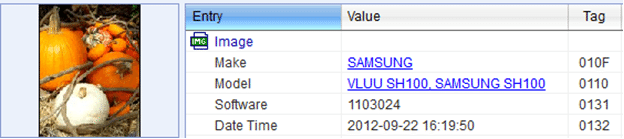
Metadata is simply extra information about a file, or some people refer to it as “data about data”. You are probably familiar with metadata but maybe not with the term itself. Have you ever right-clicked on a computer file and seen the properties? Dates, times, who was the author, when the file was last printed, etc., are all examples of metadata. For digital pictures and videos there is a specific kind of metadata that exists known as EXIF (Exchangeable Image File Format) data. EXIF data is information embedded in the image or video that can contain all or some of the information below (what is actually in the image depends on the camera manufacturer):
Make of the camera that took the picture/video
Model of the camera
Serial number of the camera
Date / time the image was taken (according to the camera’s clock)
Filename
Flash settings
Aperture settings
Image resolution
Software
And more…
A forensic computer examiner can examine a picture or video for evidence of EXIF data and use special programs to interpret the information. There are many free programs available on the Internet to do this and many photographers use EXIF data to improve their photographs. In fact, EXIF data was originally created for photographers so they could look at their camera settings stored within the EXIF data to find out what settings worked or didn’t work when taking pictures under different conditions.
Screenshot from an EXIF data parsing tool
To illustrate how EXIF data can be used to solve a crime, imagine this scenario. I was investigating a case where an adult male was suspected of having a sexually explicit conversation with a 14-year-old female via the Internet. This adult male was sending explicit text messages and it gradually escalated to him sending images of…well, you can image, to the victim. When the victim reported this to a teacher at school, our unit became involved and we forensically analyzed the victim’s cell phone.
When reviewing the pictures on the victim’s phone, we found the pictures of the suspect. None of the images showed his face and all of them were obviously taken from inside of a residence. Since he sent the messages from his cell phone, we were able to trace the phone number they came from and identify the sender. When we reviewed the pictures sent from the suspect, each image contained EXIF data. The EXIF data showed that the pictures were all taken from a Samsung cellular phone and since he had his geotagging feature enabled on this phone, each image contained the latitude and longitude of exactly where the phone was when the image was taken. This allowed me to create a Google Earth map, which happened to place a big red dot right over the suspect’s apartment.
Just from the EXIF information we could prove that the particular sexually explicit image was taken by the suspect’s phone, from the suspect’s home, at a certain date/time (since phone’s clocks are generally set by the cell phone network, they are reliable). Another critical element to prove in a crime is that of venue (proving the crime happened within a certain jurisdiction). With EXIF data, it is not difficult to prove this at all, since we know the exact GPS coordinates of the crime scene.
EXIF data has also been used to locate victims or suspects of crimes from images and videos posted on the Internet. Imagine watching a video that was uploaded to the Internet which depicted the racially motivated assault of a person. If the camera used to create the video is capable of embedding EXIF data and the website the video was uploaded to doesn’t remove EXIF data, investigators can download the video and examine the EXIF data to potentially find out more information to lead to a suspect.
While EXIF data has proven itself to be an amazing tool for law enforcement, it has also been exploited by criminals. If you have used any of the geotagging features of your favorite social media sites (Twitter, Google+, YouTube, Facebook, Foursquare, etc.) then you are aware that you can share your location with your posts and pictures. This technology is similar to EXIF data by utilizing the devices internal GPS functionality to embed your longitude and latitude into your post.
Criminals have begun using this technology as another tool for cyberstalking. By downloading images and videos that people post to their personal websites or social media sites, tech-savvy criminals can do the same technique law enforcement employs to locate where someone was at when they created the image. If you are a victim of stalking or have been threatened by someone in the past and have gone to great lengths to hide from them, all it would take is them getting ahold of one image placed on a social network site taken by your cell phone or high-end digital camera with built-in GPS. If that picture was taken at your home, work, child’s school, etc. that’s all they would need to find you. It’s a scary thought and one that people must consider when using this kind of technology that is generally turned on by default.
Josh Moulin
Josh has a long history of public service, beginning in 1993 as a Firefighter and EMT. After eight years of various assignments, Josh left the fire service with the rank of Lieutenant when he was hired as a police officer.
Josh spent the next eleven years in law enforcement working various assignments. Josh worked as a patrol officer, field training officer, arson investigator, detective, forensic computer examiner, sergeant, lieutenant, and task force commander.
The last seven years of Josh’s law enforcement career was spent as the commander of a regional, multi-jurisdictional, federal cyber crime task force. Josh oversaw cyber crime investigations and digital forensic examinations for over 50 local, state, and federal law enforcement agencies. Under Josh’s leadership, the forensics lab was accredited by the American Society of Crime Lab Directors / Laboratory Accreditation Board (ASCLD/LAB) in 2009.
Josh has been recognized as a national expert in the field of digital evidence and cyber crime and frequently speaks across the nation on various topics. He has testified as an expert witness in digital forensics and cyber crime in both state and federal court on several occasions. He also holds a variety of digital forensic and law enforcement certifications, has an associate’s degree and graduated summa cum laude with his bachelor’s degree.
In 2012 Josh left law enforcement to pursue a full-time career in cyber security, incident response, and forensics supporting a federal agency. Josh now leads the Monitor and Control Team of a Cyber Security Office and his team is responsible for daily cyber security operations such as; incident response, digital forensics, network monitoring, log review, network perimeter protection, and firewall management.
background: #bd081c no-repeat scroll 3px 50% / 14px 14px; position: absolute; opacity: 1; z-index: 8675309; display: none; cursor: pointer; top: 252px; left: 20px;”>Save








Thanks for the kind words SZ…sounds like a strange device those guys used for sure! Take care.
Ok Josh, you have scared the children !
That is scary about the malware. When I went through ID Theft they used my credit card to buy a device that allowed them to call, however the numbers all came out 0000000. They even called me ! I cant remember the device name now. Not sure why such a device is even necessary.
ps how is it you still look 20 ?!
MYG,Josh, I didn’t even thing about that. Scary for sure.
Pat,
You bring up a whole different area about the geo-locating of social media events. Imagine that you have a friend stay at your home for a few days and that friend has a very bad person who is looking for them. Your friend decides to tweet, post on Facebook, “check-in” on Four Square, and upload a new video to YouTube. The bad guy tracks them back thanks to the geo-locate information in their social media posts and guess where it returns to? That’s right, you’re house!
Josh
Thanks for this!!!!
Lynette,
What you’re describing would be very difficult to do. SIM cloning is something that has been around for years, but it doesn’t really work like what you are talking about. SIM cloning (or ESN cloning for non GSM phones) allows another person to make fraudulent phone calls using the customer’s number and all the charges go to the customer since the phone company can’t tell who actually made the calls.
What is easier to do though is infect the victim’s phone with some malware. Having a malicious spy application on the victim’s phone could allow the suspect to see in real-time exactly where the phone is on a Google map, get copied on all incoming/outgoing text messages, listen in to telephone calls in real-time, turn on the phone’s camera to see its view, and turn on the microphone even if the phone isn’t being used.
Hopefully that helps.
Josh
Jenna Blue – you are very welcome, I hope you can use this in your next book too!
Josh
Jena – absolutely! I would be happy to help you out. Just let me know if you need anything from me.
Josh will be here to answer your questions in just a bit. He’s on west coast time (and, he’s out fighting crime 🙂
Josh, Thanks for taking such time with this post. Incredibly informative. A bit scary that criminals can use it, but heartening that crimes are being solved because of it, too.
Lee, thanks for inviting Josh! Makes me itch to include these storylines in a book!
Best,
Jenna Blue
Wow, I am a little phobic about having my picture taken and have recented it when people take pictures at a meeting or event and then post them on social media. I’m from the old school of you need permission first to do that. This situation posses a whole new area I didn’t even realize existed. Scary for sure. I’m going right in to talk to Hubby about his camera and cell phone pictures. Thanks you, Josh and Lee.
Hi Josh: Is there a way someone could receive the phone calls and messages from someone else’s phone? Remove the Simm card? For my WIP I need to find a way that ‘he’ gets no messages at all on his phone, but ‘she’ is getting them all. Is this even possible? Thank you so much for your time. Lynette
Hi Josh,
I’m a crime writer and reader, but in my day job, I’m the production editor of a quarterly newsletter for the Alberta College of Social Workers. In our last issue, we featured a story on stalking and another on maintaining online confidentiality, and the information you gave on geotagging and social media sites would make a great follow-up piece. Could we have your permission to reprint an excerpt from your post? It would probably be no more than 500 words, and would include your byline, a brief bio. I would send you a draft for your approval.
Thanks for a great post!
Hi Sz, you’re very welcome.
Not all images are going to have EXIF data that are online, and even if EXIF data was present in the picture you won’t always find a longitude/latitude embedded into it. Sometimes EXIF only has things like date/time digitized, camera make/model, flash settings, etc. It really depends on the camera that was used to take the photo.
There are many programs available to view EXIF data in a photograph and there are even free add-ons for your favorite browsers. If you like to download the photos, or want to check EXIF data in your own pictures, I like Opanda IExif viewer. It’s a free program that works very well. If you are interested in looking at EXIF data directly through your browser, search for an EXIF reader. For example, in Firefox I have an add-on called Exifviewer that I use.
When using Firefox, all I have to do is right click on any image that is displayed in my browser and then select “view image exif data”. A window will appear showing you any EXIF data that is available.
Thank you Josh , I always enjoy your posts. They are very informative and usually a bit scary.
So if you go to a facebook page and click on a photo, are you saying anyone can right click and get properties or is it a special program you go into to get this info ?
When I tried on a random photo in the newspaper it did give some info. I was surprised both dates were todays and the artical must have been written a few days ago. It was a house for sale type artical.
Hi Diane,
You’re welcome for the post, I’m glad you found it helpful. I’ll try to answer your questions.
Turning off the geotagging function on your mobile devices is usually found in the general or privacy settings. The only downside is this function is also usually associated with your GPS functionality, meaning if you disable geotagging in your photos, you are also turning off the same GPS chip you use to navigate. Most people I know turn off the feature so they don’t accidentally take pictures with their location embedded in them and then specifically turn on the GPS when they want to navigate. This is a pain, but just remember that convenience is the antithesis of security!
If you are using social media apps on your mobile devices (Facebook, Twitter, Google+, etc.) then just be careful not to include your location with your posts (if this is something you are worried about). Most of these sites are now offering this as an option instead of posting it by default. You should double check your security settings and make sure you have not turned on sharing your location with each post by default.
Some websites parse out the EXIF data when you upload an image to their site, because it is just more information to store. This is not always the case though, and on websites that focus on geo-locating your photos (Flickr and Picasa for example), the information will not be removed when you upload pictures.
As far as advise on keeping yourselves safe from Internet sexual predators…that could be an entire series of blog posts. As it relates specifically to today’s topic though, I would make sure you limit who can see your photos if you are using geotagging and be cautious what photos are posted on the Internet using mobile devices. Turn off your geotagging functions if this is something that concerns you. If you have a GPS chip embedded in your digital camera, see if you can turn it off, or use a program that will strip out the EXIF data from your pictures before you upload them to the Internet.
EXIF data isn’t all bad of course and geotagging has some really great features. Imagine going on vacation and having the exact GPS coordinates of everywhere you took a photograph and you can overlay that on a Google Earth Map. My goal is to make people aware of the technology and how the criminal element may exploit it.
Thanks for reading!
Thanks for posting this, Lee, and Josh for writing it and sharing the info. I shared it privately with some writers, and a few family and friends. Here are some of their comments/questions:
A. So, how can be turn the EXIF data off or have it not show???
B. Very interesting article. I knew about the info embedded in photos since i have one of those cameras, but I didn’t know it was available to anyone with a program to read it and that the info followed the photo.
C. Yes, they can. Don’t post i’d you don’t want it public. My hacker-hubby could tell you stories…! Lucky he’s a white-hat.
And mine – I gather that we can help hide “where we are” information by not using these social media on our phones, for a start. It seems that any picture taken by a cellphone is likely to capture all this data, regardless, so that if we post a picture on FB that is taken from our cellphone, the date/time of that picture as well as the location, is available to anyone who right-clicks on the photo? So we have to limit access to friends-only at the very least (and hope none of our FB-friends are pedophiles, or related to the same)? Twitter is wide-open, so we should be careful what information is at any personal links we provide? Any advice on what we can do to protect ourselves from online predators would be greatly appreciated. Thanks!!!!!