Lt. Josh Moulin: How Computers Are Used in Missing Persons Cases
Lieutenant Josh Moulin supervises the Central Point Police Department’s Technical Services Bureau and is the Commander of the Southern Oregon High-Tech Crimes Task Force. He is one of approximately 470 Certified Forensic Computer Examiner’s worldwide and has been trained by a variety of organizations in digital evidence forensics. Lt. Moulin has also been qualified as an expert witness in the area of computer forensics and frequently teaches law enforcement, prosecutors, and university students about digital evidence.
Beginning his public safety career in 1993, Josh started in the Fire/EMS field working an assortment of assignments including fire suppression, fire prevention, transport ambulance, and supervision. After eight years Josh left the fire service with the rank of Lieutenant and began his law enforcement career. As a Police Officer Josh has had the opportunity to work as a patrol officer, field training officer, officer in charge, arson investigator, detective, and sergeant.
For further information about the Central Point Police Department please visit www.cp-pd.com, and for the Southern Oregon High-Tech Crimes Task Force visit www.hightechcops.com. To reach Sgt. Moulin you can e-mail him at joshm@hightechcops.com.
How computers are used in Missing Persons cases
Many law enforcement agencies across the United States are incorporating computer forensics into traditional missing persons investigations. There are few things that provide a better window into a person’s life than the hard drive of a computer.
In our digital evidence forensics lab we regularly assist law enforcement agencies who are trying to locate missing people. After obtaining a computer used by the missing person we pour through the hundreds of thousands of files in an attempt to determine who they were last talking to, where they may be going and why they left.
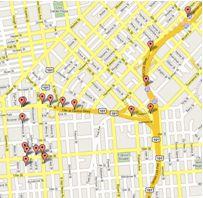
In one particular case our lab assisted in locating an adult female who had been missing for several weeks. We uncovered some deleted Internet history files showing her using Google maps to find places in an adjoining state. We also found deleted files of her using her credit card to purchase travel tickets to a specific area that later proved to be exactly where she was at.
There have been documented cases where the forensic examination of a computer has led to finding a missing person, and in some cases has led to the arrest of a suspect. On the East Coast of the United States a law enforcement agency performed a forensic examination of a computer that belonged to a missing young woman. During the forensic examination, electronic correspondence was found between the missing woman and another person. After court orders were issued to reveal the true identity of the person she was communicating with, police identified the person as a man living in an adjoining state.
When the police arrived at this man’s door and continued their investigation they ultimately discovered the missing woman’s body buried in the backyard.
Other items of interest can be found on a missing person’s computer as well. E-mail messages, blog postings, MySpace comments, online banking activities, computer journals, etc. can all be used to help locate someone.
Sometimes the computer isn’t as important as knowing what accounts are used by a missing person. For example, during a forensic computer examination, online accounts are located such as MySpace, Yahoo!, Gmail, Hotmail, etc. By serving simple subpoenas on these companies information can be obtained about where they are checking their e-mail or logging into a website from. Sometimes this information is particularly useful in runaway cases where a juvenile doesn’t want to be found but continues to check their web-based e-mail accounts while they are on the run.
* * *
The Bulletin Board
Author SJ Rozan is running a contest on her blog http://www.journalscape.com/sjrozan/2008-10-19-08:34. Stop by and win an ARC of her her wonderful new book SHANGHAI MOON. If you’ve never read any of SJ’s books do yourself a favor and pick up a copy right away. She’s a brilliant writer.
This week is urban fantasy week on literary agent/author Lucienne Diver’s blog http://varkat.livejournal.com/ . Today’s post is a wonderful and original short story by author
Rachel Caine. She’ll also have Faith Hunter, Marjorie M. Liu, Laura Anne Gilman, Diana Pharaoh Francis and Susan Wright blogging, among others. By the way, Lucienne has a new book coming out. I had the chance to see the cover art and it’s fantastic.
Don’t forget to enter the 200 word short story contest right here on The Graveyard Shift. Your stories will be judged by Alfred Hitchcock Mystery Magazine editor Linda Landrigan. For details click here.
background: #bd081c no-repeat scroll 3px 50% / 14px 14px; position: absolute; opacity: 1; z-index: 8675309; display: none; cursor: pointer; top: 1657px; left: 20px;”>Save







Thanks! I tried tracing my ISP on WHOIS and it told me it was Roadrunner in Herndon VA. Since I’m in Florida, that wouldn’t have done my bad guy much good — or me, since I’d hoped they could have traced my heroine’s whereabouts because she sent an email, but I managed to figure out another way to deal with that plot point.
Will – Think about a computer like a book with pages and a table of contents. When you delete something from a computer, all it really does is remove the entry in the table of contents, but the “page” is still in the book and nothing happens to it. Using forensic techniques the “page” with all the data can be recovered and linked back to where it once existed (most of the time).
The computer will see an opening in the table of contents and it can reuse that area to put new data in its space. With the size of hard drives these days and with how computers write data to a hard drive, it can take a very long time before that old page that you deleted is actually overwritten making it possible to recover evidence that is years old.
As for the web based e-mails being stored locally on your computer, my answer is, it depends. Some e-mail clients (like Outlook) have the ability to select an option to keep e-mails on the server AND download them. This way if you have a computer downloading your messages, but you still want to check them from another computer on the web, they aren’t gone forever. In this mode Outlook basically copies the messages instead of moving them.
With most e-mail servers deleted messages are kept for a period of time. Depending on legal requirements and hard drive space issues they may be kept for a long time, or a very short time. Just like computer forensics however, even if a message is “deleted” from an e-mail server it can most likely be recovered using forensic techniques.
For example in the City I work for, e-mail messages are kept for 90 days after they are “deleted” by the user in case we have an litigation or a user accidentally deletes something and they want it back.
I hope this helps.
Terry – You are correct that you cannot trace IP addresses without serving a subpoena to the Internet Service Provider (ISP). You don’t necessarily have to be law enforcement, but you do need a subpoena.
For example, civil attorneys will serve subpoenas on ISP’s to find people who are distributing music and movies against copyright laws, so it isn’t always the police who have exclusive access to this information.
You can however find geographical locations based upon IP addresses with no special information. For example, if you have the IP address of a sender you can use a website (Maxmind.com is popular) to find where that IP comes back to geographically. This isn’t always 100% accurate, but it normally is close.
Question: My research indicated that if you’re NOT in law enforcement, tracing an email back to the place from which it originated isn’t all that easy. I used the headers in my own messages and all I could tell was that it came from a roadrunner account, and the address was listed as corporate headquarters.
Can “Joe Q. Public” actually figure out where someone is, based on an email they sent? At first I thought so, but I’ve had to rethink that plot element.
Thanks, Lee. Funny thing is, in the climax of my first novel, my protag gets clues to a virus’ origin from a computer using the web browser history and the last documents feature in MS Word and Excel. SImple computer forensics, but effective.
I thought the same thing as Will.
Also, did you work the Cole Puffinburger case ? I was glad they found him ok.
Will – Great questions. I’m going to let Josh answer them since he’s the expert. He’ll be checking in a little later. His time zone is three hours earlier than here in Boston.
Another great topic, Lee and Josh. I have a question? When is a computer file REALLY deleted?
Also, if you use an email program like Outlook and you load email to your computer from your email provider, removing them from the server as you do, are they really gone from the server, or can they be reovered from the provider?